Tatsu recently experienced a major vulnerability, thousands of our customers who’re using the lower versions of the Tatsu plugin on their site are affected by this vulnerability.
We were taken aback by the sudden barrage of critical customer support tickets, without wasting time we spun into action and created a QRT to mitigate the vulnerability.
As per the initial investigation by our Security Team, someone exploited a vulnerability in the Tatsu Plugin and created a virus that modifies the core PHP files while also creating new files.
We were fully aware of this vulnerability which was initially identified in one of our security audits. We had fixed this vulnerability with a plugin update. However, some of the sites that were still running on the lower versions of the Tatsu plugin got affected by the vulnerability.
The vulnerability can be fixed with a Site Cleanup and a plugin update.
Step 1: How to do Site Cleanup?
1. Delete all newly created files.
Newly Created files will be something like this: You need to delete these files.
wp-option.php
wp-special.php
/uploads/typehub/custom/dn46/.clone.php
/uploads/typehub/custom/dn46/.class.php
/uploads/index.php
/uploads/typehub/custom/dn46/.demo.php
/uploads/typehub/custom/tatsu/.shell.php
/uploads/typehub/custom/dn3/.class.php
/uploads/typehub/custom/ccpl/
/uploads/typehub/custom/tastyy/
wp-content/uploads/typehub/custom/dn2/.class.php
wp-content/uploads/typehub/custom/dn2/demo.html
wp-content/uploads/typehub/custom/dn2/class.html
wp-content/uploads/typehub/custom/dn2/class - копия.html
2. Restore all the modified files.
Modified files: wp-blog-header.php
wp-content/index.php
To restore this file:
- Download the WordPress Zip from wordpress.org.
- Extract the zip in your computer.
- upload the wp-blog-header.php file to your server this will replace the modified wp-blog-header.php file
You can perform these tasks manually: Use FTP or File Manager provided by cPanel to clean up the files.
3. Post Clean-Up Activity
- Clear your cache (wp-rocket or plugin cache, DNS cache, server cache).
- Check if your website is working fine
Step 2: Update Tatsu Plugin to the Latest Version
Click on the Download Tatsu button to download the latest plugin zip. Upload the zip as a plugin in WordPress and it’s done.
Here’s How to Fix Site Redirection
Even after the site clean up and Tatsu update if you find that your site is being redirected to another unknown site then follow the below-mentioned steps:
Step 1: Search your database for an unknown script
Users are reaching out to us saying their site is being redirected to an unknown site. After further investigation in the database, it was found that a malicious script has been embedded after every paragraph that redirects a user to another dummy site.
You would need to perform a check on your server, you can take the help of the server support to identify the malicious script if any.
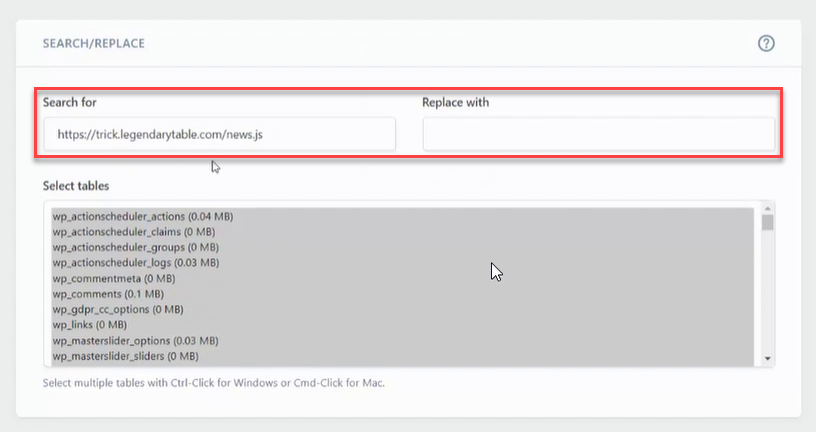
Step 2: Replace the Identified Script with Blank Spaces
Sample Script:
Once the script has been identified, you need to install the Better Search Replace plugin and replace the redirection link with a blank space.
Replacing the script with blank space will solve the issue and your site will be back to normal.
Get Help
After performing the above activities Check if your website is working fine, if not contact [email protected] right away.